One of the main activities of the CAE-C-Expansion Project is a comprehensive research study that guides key steps of the project and adds to the body of knowledge in Cybersecurity education.
Research Study Design
Title
Enhancing Aspiring Cybersecurity Professionals Writing Skills: An Evaluation of Student and Work Force Needs for Program Improvement
Problem
Students in rural schools are often missing communication skills when they enter college and the work force. Lack of effective communication skills impacts their potential to thrive and excel in work setting-whether in terms of effectively giving instructions to others, writing clear memos and e-mail messages, or negotiating everyday conflicts in work settings. Moreover, these students often believe a technical field requires only hard skills like Math and Science, not communication skills like writing and speaking. As these students graduate, enter the work force, and then seek advancement in their field, their lack of communication skills restricts their opportunities for leadership and collaboration.
Purpose
The purpose of this study is to conduct a comprehensive mixed-method research study to identify writing and communication challenges faced by (a) current students enrolled in computer science courses, (b) professionals who are engaged in the cybersecurity field.
Population
The population for this study is undergraduate computer science majors at rural schools in Western Pennsylvania.
Sample
- Survey Respondents: The 203 students enrolled undergraduate courses were invited to participate in the quantitative phase of the study; 86 students completed the survey.
- Interview Participants: 27 professionals engaged in cybersecurity work at various institutions were invited to participate in the qualitative phase of the study. These professionals included, but were not limited to those involved in:
- System administration; client systems and servers;
- Network administration and network security operations;
- Security assessment, security auditing and information assurance;
- Threat analysis, intrusion and data analysis, intelligence and counter intelligence;
- Forensics investigation;
- Programming;
- Technical writing;
- Security architecture and engineering; and
- Information security and incident management. (Evans & Reeder, 2010, p. 27)
Research Design
The interdisciplinary research team utilized a Congruent Design (Ivankova et al., 2006) which is very similar to Creswell's (2012) Mixed Method Triangulation Design (QUAL+QUAN). The design is depicted in Figure 1.
- Download the approved Qualitative Research Protocol
- Download the approved Quantitative Research Protocol
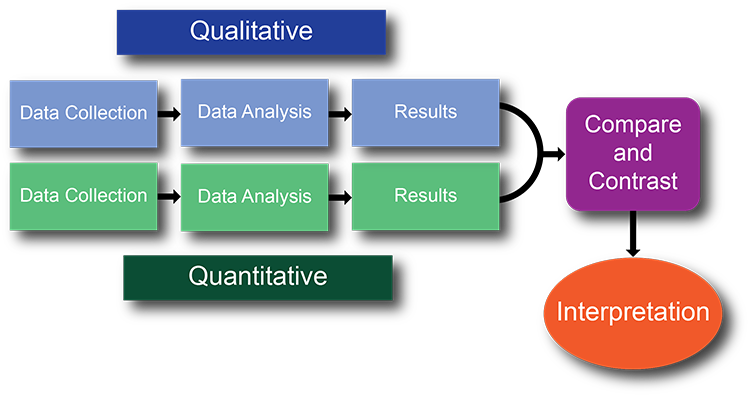
Figure 1. Congruent Mixed Methods. Adapted from "A Framework for Mixed Stakeholders and Mixed Methods" by B. Crump and K. Logan, 2008, The Electronic Journal of Business Research Methods, 6(1), p. 21-28.
For additional information about this research design, visit:
Research Timeline

Research Questions and Data Sources
The researchers employed a three-phase approach to develop and validate both instruments. Table 1 illustrates how data collected though three different sources will be used to answer the five research questions.
| Research Questions | Survey Instrument Item No. | Interview Protocol Item No. | Extant Data |
|---|---|---|---|
| 1. Which technical courses (past and current) did aspiring cybersecurity professionals identify as valuable? | 8-10 | 11 | |
| 2. How do aspiring cybersecurity professionals describe their present skill level in terms of writing and communication? Are there group differences based on gender, student status (freshman, sophomore, junior, senior), linguistic background (mono/bilingual/multilingual) and major (MIS/COMSC)? |
1-6 12 13 |
||
| 3. What kinds of writing do practicing cybersecurity professionals do most often? What challenges, if any, do they face (writing type, writing skills)? | 2-6 | ||
| 4. What resources should Computer Science Professors and the Writing Center offer to better meet the needs identified by aspiring and practicing cybersecurity professionals? |
10 13 |
12-13 | X |
| 5. Does extant data, collected by the Writing Center, show an increased use of the services they offer undergraduate students over a period of two years? | X |
Instruments
Details about the two data collection instruments are presented below.
- Survey: The survey protocol includes 14 questions. Items 1-7 elicit the following data from survey respondents: class standing, gender, spoken language/s, college major, and potential future careers. Questions 8-10 required survey respondents to identify the courses they found helpful in high school and those they would have liked to take to be successful as a computer science professional. Item 11 assesses survey respondents' beliefs about the importance of writing skills and oral skills in the fields of computer science and cybersecurity. Items 12-13 examine survey respondents' beliefs about oral and writing skills, use of feedback in improving these skills, and resources that they used to improve their writing. Finally, item 14 requires survey respondents to describe the number of times they visited the different writing center sites for tutoring.
- Interview Protocol: The interview protocol includes 17 core questions. Item 1 explores the nature of the interviewees' jobs. Items 2-6 assess the interviewees' past and current writing experiences. Items 7-9 elicit data related to the interviewees' oral presentation skills. Items 10-13 elicit data related to interviewees' beliefs about important skills for a colleague and recommendations that would enhance undergraduate computer science students' learning. The last four items, 14-17, elicit interviewees' demographic information and request for the interviewee to review the interview transcript.
For additional information and/or access these instruments contact Crystal Machado, principal investigator, cmachado@iup.edu.
Key Findings
Research Team
Dr. Crystal Machado, graduate assistants Krista Sarraf, Amber Stewart, Jennifer Baggett, Zhengqi Hu, and doctoral students enrolled in ALS852 School Evaluation, Fall 2017 and CURR 983 Analysis of Qualitative and Mixed Method Data in Education, Spring 2018
References
Evans, K., & Reeder, F. (2012). A human crisis in cybersecurity: Technical proficiency matters. Washington, D.C.: Center for Strategic and International Studies. Retrieved from https://csis-prod.s3.amazonaws.com/s3fs-public/legacy_files/files/publication/101111_Evans_HumanCapital_Web.pdf
Crump, B., & Logan, K. (2008). A framework for mixed stakeholders and mixed methods. The Electronic Journal of Business Research Methods, 6(1), p. 21-28.
Possible References
Creswell, J.W. (2012). Educational research: Planning, conducting, and evaluating quantitative and qualitative research. Boston, MA: Pearson.
Ivankova, V., Creswell, J. W. & Stick, S. L. (2006). Using mixed-methods sequential explanatory design: From theory to practice. Field Methods, 18(1), p. 3-20.